We are proud to announce the 18.0 release of Topicus KeyHub. This release brings a completely new way of authorizing clients to act on their own, allowing further automation with KeyHub without compromising your security. We've also worked hard to further improve the stability of our high availability solution. This release also brings many small usability improvements. As usual, a number of smaller improvements have been made and several issues have been fixed.
Client permissions
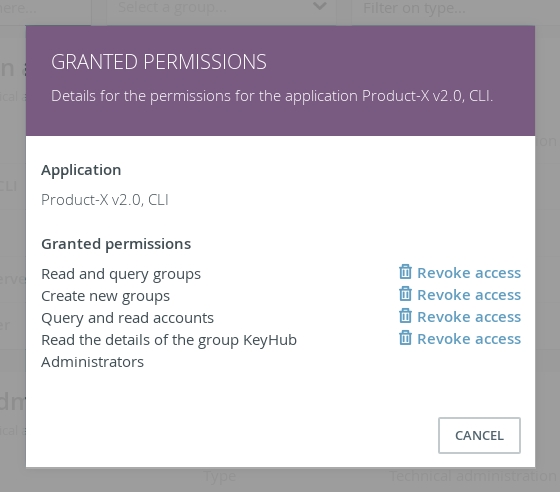
TKH-1650 TKH-1677 Traditionally, OAuth2 clients using the client credentials grant only had a limited set of fixed permissions in Topicus KeyHub. It was possible to grant access to vaults and to some details about groups. With 18.0, this has become a lot more flexible. It is now possible to grant clients permissions ranging from queries on accounts or groups to deleting accounts or creating groups. Naturally, it is still possible to grant access to vaults. All previously granted permissions are automatically converted to the new model.
In the future we expect to add many more permissions to this model. If you have specific needs for permissions, please contact us.
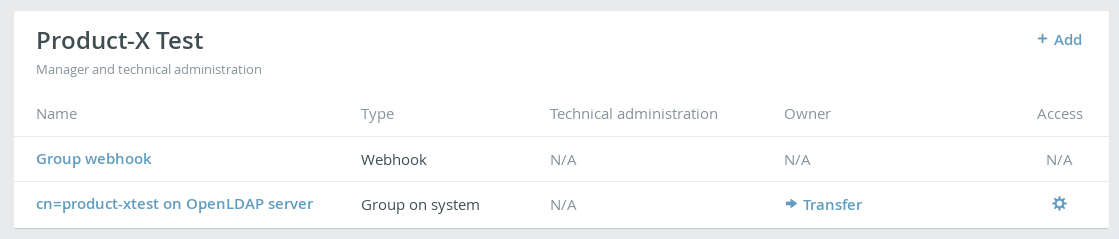
Webhooks for group managers
TKH-752 Webhooks for groups no longer fall under the domain of KeyHub administrators. These webhooks are now managed by the groups themselves. A group manager can easily create a webhook to deliver all audit records relevant for that group to a certain endpoint.
Add claims to the id_token
TKH-1689 The OpenID Connect protocol by default only puts a very limited number of claims in the id_token. Some applications incorrectly assume that claims that reside in the userinfo endpoint are automatically also placed in the id_token. It is now possible to configure KeyHub to add these claims to the id_token, even when the application does not explicitly request them. This makes it possible to use OIDC with some applications that do not strictly comply with the standard.
Improvements to the appliance
We've received a lot of feedback on our appliance and the configuration of high availability. In 18.0, we've made many smaller and bigger improvements to enhance the stability of a cluster and to prevent accidental data loss. The following issues were resolved for our appliance:
TKH-1630The docker containers now run with read-only filesystems making it much harder to exploit a potential vulnerability.TKH-1652The appliance manager no longer reads the settings from Topicus KeyHub itself. This could cause the appliance manager to become unresponsive in the event of a problem with the application itself.TKH-1659When applying configuration changes in a cluster, the appliance manager will no longer stop on the first error but will continue to apply the configuration on other nodes. This makes it possible to repair a cluster when one node is unresponsive.TKH-1662An action button was added to synchronize the configuration of a single node in the cluster.TKH-1663When adding a new node to the cluster, the new node is now always configured last. Previously, existing nodes in the cluster could refuse the connection of the new node, because they did not yet get the new keys.TKH-1664Let's Encrypt certificates are now correctly renewed when synchronizing the configuration.TKH-1665Synchronizing the configuration on new nodes in a cluster no longer results in an error when some required information was not yet gathered on that node.TKH-1679It is no longer required to specify ports in the firewall configuration for the monitoring zone. If no ports are specified, only TCP port 9443 is exposed.TKH-1680Specifying TCP port 9443 for the monitoring zone no longer gives a error.TKH-1684An error was fixed when upgrading an older version of KeyHub to 17.2 or later.TKH-1691When restoring a database on a node in the cluster, the appliance manager now warns when it detects potential data loss, such as when trying to restore an empty database over a non-empty one.TKH-1693The appliance will no longer automatically restore snapshots that are over 4 hours old. This prevents data loss when a snapshot was not properly removed on a previous update. It is still possible to manually restore such a snapshot.TKH-1694Trying to restore a backup that lacks certain configuraton files should no longer result in an error.TKH-1698Pgpool was updated to the latest version, 4.2.2.TKH-1706Rewinding on failover is now more reliable, reducing the chance on the need for a full base backup.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1578When using multiple directories, Topicus KeyHub will now automatically ensure usernames are unique by adding a number suffix when usernames would otherwise conflict.TKH-1584It is now possible to navigate between the source and target vault of a shared vault record if you have the permissions to view both.TKH-1623When copying or moving a vault record to a vault where you don't have the permission to remove it, you are now asked for confirmation first.TKH-1635The documentation on expired vault records was updated with more screenshots.TKH-1640Several improvements were made throughout Topicus KeyHub to make the application easier to use with a screen reader for visually impaired users.TKH-1641The button to share, copy or move a vault record is made much more prominent to make it easier to find.TKH-1644The installation guide for Topicus KeyHub on Azure was revised.TKH-1645Many improvements were made to our testing infrastructure to greatly reduce the duration of the build while at the same time improve the reliability.TKH-1656The feedback on badly formulated queries via the CLI has been improved.TKH-1658Some styling improvements were made to the launchpad.TKH-1666An error was fixed that prevented KeyHub administrators from accessing the list of accounts for private groups.TKH-1667The vaults page will now correctly always load all appropriate entries when changing the filtering.TKH-1674It is now possible to create multiple provisioning groups in one call when creating a group on system via the API.TKH-1678An error was fixed that prevented the dashboard from loading when a private group requested authorization.TKH-1682The Feature-Policy/Permission-Policy header was updated to prevent warnings in some browsers.TKH-1683Several irrelevant options are no longer displayed when configuring the first directory during installation.TKH-1686The documentation for importing vault records via the CLI was fixed.TKH-1688Passwords are now copied directly to the clipboard using the new async clipboard API. This works in all major browsers, with the exception of Safari.TKH-1690A textual error was fixed when displaying audit records about expired vault records.TKH-1695The manual about restoring backups was revised.TKH-1697The application server was upgraded to WildFly 23.0.1.TKH-1703It is now possible to store files up to 2MB in the vault.TKH-1708Thevault writecommand with the--fileparameter now correctly uploads the contents of the file, instead of the file name.

